Pickle Rick - TryHackMe
Each year, I take part in Advent of Cyber with Andy Hancock. I'm obliged to say "of Hancocks VMware Half Hour because promotion and branding! But seriously, Andy is a top bloke and you should check out all his videos.
This lovely little tradition originally started when I was part of Freeside at the University of Hull, we would do it as a team (or at least, the ones who wanted to participate), but since I've left both the University and Freeside, Andy and I have been doing it together. He's a bit more enthusiastic than me about maintaining his TryHackMe streak, at the time of writing, he has about a 300 streak score - meaning he's maintained his streak by doing at least one hacking challenge per day, every day so far since the last Advent of Cyber.
With that in mind, and only a few months until the next Advent of Cyber (December), I figured it's probably time to get the grey cells working and complete some rooms. Today's was called "Pickle Rick" and involved attacking a web server to find 3 flags to successfully turn Rick back into a human - fans of Rick & Morty will know the meme well.

Initial Exploration
After the server and attack box had booted up, we were off.
As with all hacking endeavours, some initial exploring was in order. I was assigned the IP Address 10.10.4.232 so, naturally, the first step was to see what we had when visiting the server/web page. Maybe all the answers would be listed nicely and neatly for me, right?
Unfortunately, I was greeted by a very basic page with not very much information at all. No problem... using cURL in the terminal to spit out the web pages code revealed that someone had carelessly left a username within a commented out section of code - perfect. That's a start, the username was: R1ckRul3s.
As the index suggested there was a login page, I needed to find it. /login didn't work, nor did some of the other basic guesses - so I moved to dirb http://10.10.4.232/ to see what files and directories were available. As it happened, it returned an assets directory and a few other files, including a robots.txt.
Reading the robots.txt gave Wubbalubbadubdub, which is unusual for a robots.txt file to say the least so I noted it down as it may come in useful later.
Getting In
I still didn't have a login page, so I turned to Nikto. A tool that scans web servers for vulnerabilities, including, according to the docs -
- Find SQL injection, XSS, and other common vulnerabilities
- Identify installed software (via headers, favicons, and files)
- Guess subdomains
- Includes support for SSL (HTTPS) websites
- Saves reports in plain text, XML, HTML or CSV
- “Fish” for content on web servers
- Report unusual headers
- Check for server configuration items like multiple index files, HTTP server options, and so on
- Has full HTTP proxy support
- Guess credentials for authorization (including many default username/password combinations)
- Is configured with a template engine to easily customize reports
- Exports to Metasploit`
The perfect tool to find a login page, right? I ran nikto -g 10.10.4.232 and it found the login page at /login.php. Bingo.
Below is a preview of the portal with the credentials collected:
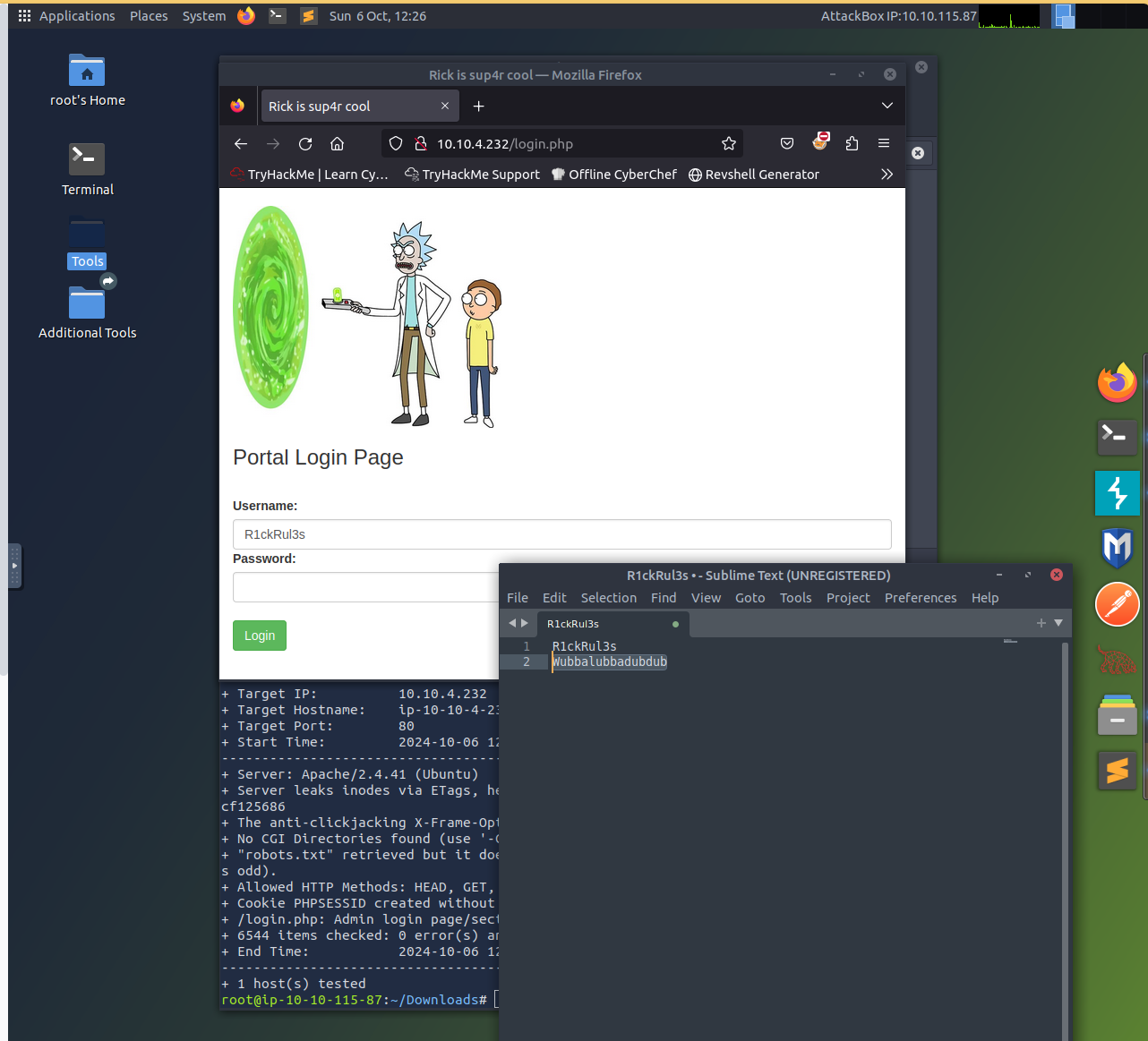
Entering the login details collected earlier from the code and robots.txt, I was in.

The Portal
Once logged in, I was a bit stumped. I was presented with a command panel and a few other pages that were off limits and only viewable to the "REAL RICK". I also couldn't find any documentation or clues for the commands.
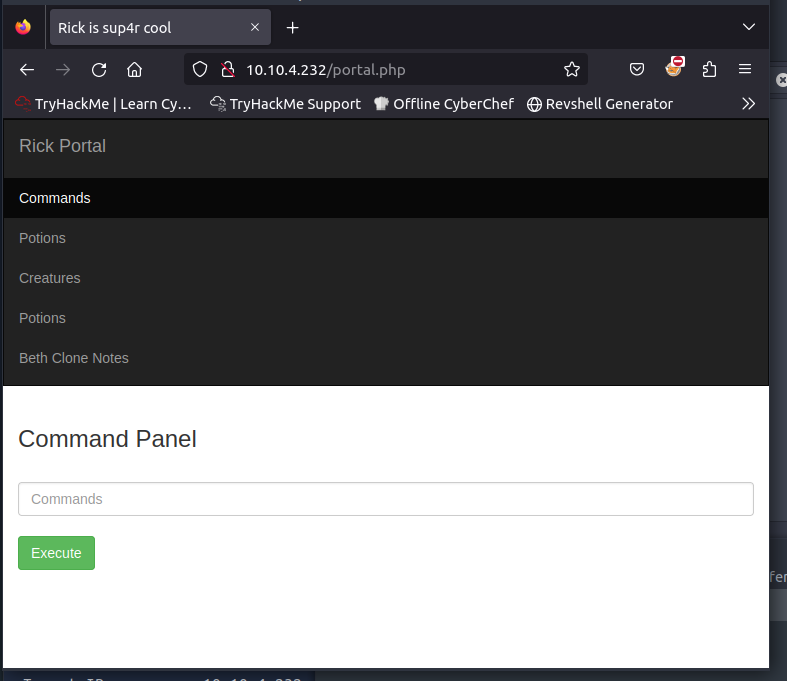
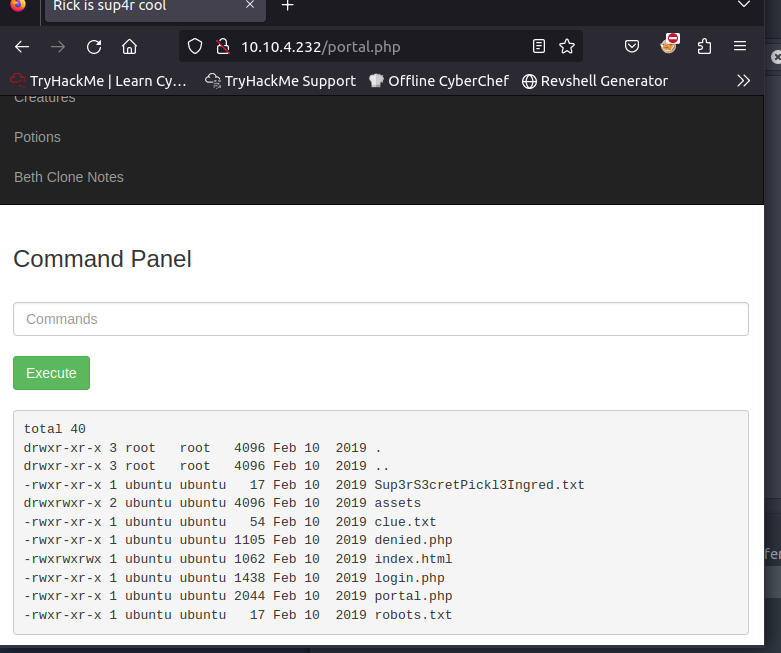
After a good 10 minutes of pondering, I figured if the server was running a Linux distro, it might be worth trying some linux based commands - and it worked. ls -la returned a list of files and directories, including the first flag. It also returned clue.txt which suggested that I should keep looking around the file system for other ingredients (flags).
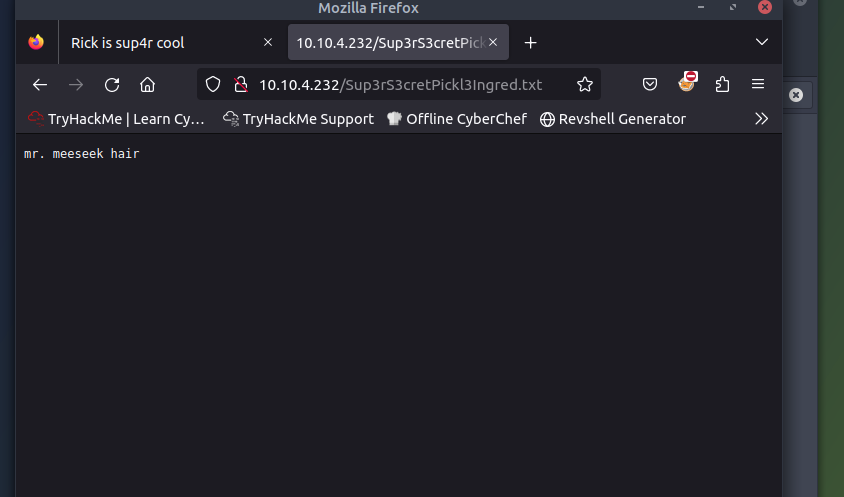
Opening the first flag in the browser, I was able to establish that the first ingredient was mr. meeseek hair. That left two to find, by exploring the file system.
Using my knowledge of Linux, it seemed appropriate to try the /var/www/, /home/{user}and /etc/ directories. Unfortunately, I hit a roadblock in that some commands were restricted/disabled. This made an otherwise simple task a bit more challenging, because I couldn't just cd into a directory or use nano or vim to read a file if I managed to list it.
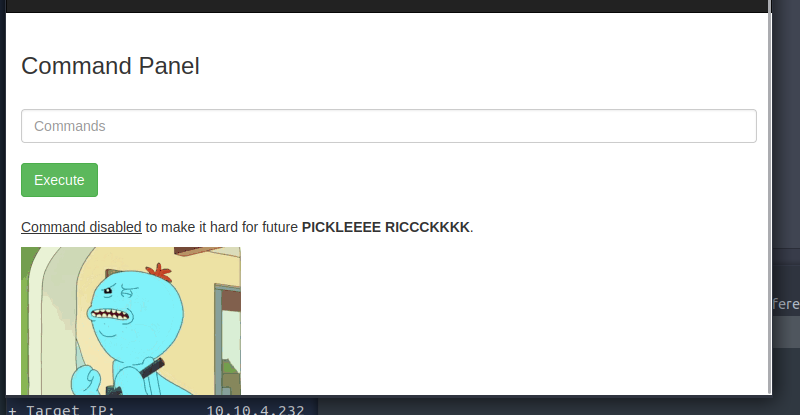
When I saw the command disabled message, I did think..

however... If I couldn't execute these commands with the permissions currently assigned to the user I was logged in with, perhaps I could switch user? I decided to try to sudo su root to see if I could switch into the root user and amazingly, it worked! No password prompt or anything.
All that initial worry turned into..

With the relevant permissions, I began to navigate around the file system trying /home/rick first. There was a directory called second which contained the second flag - 1 jerry tear.
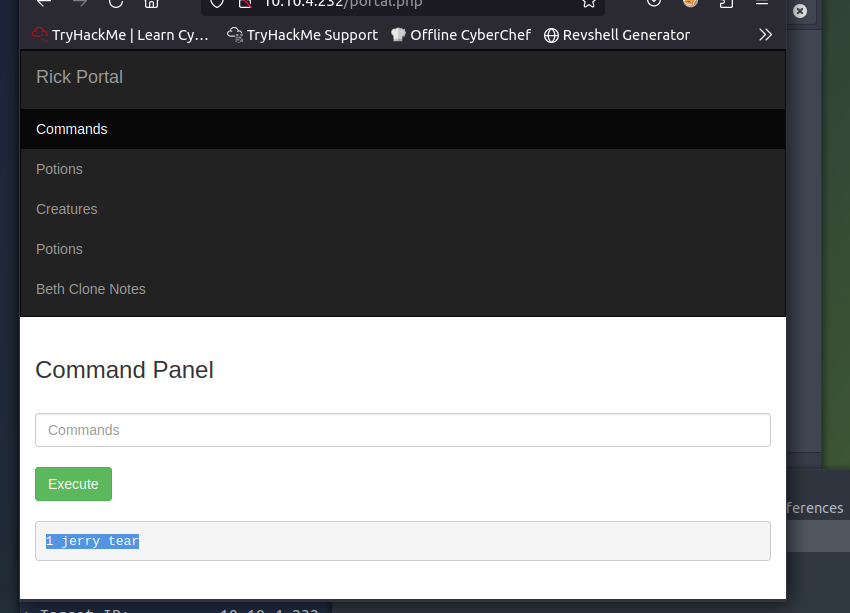
The third flag was located in /root in a txt file called 3rd.txt and contained the final ingredient - fleeb juice.
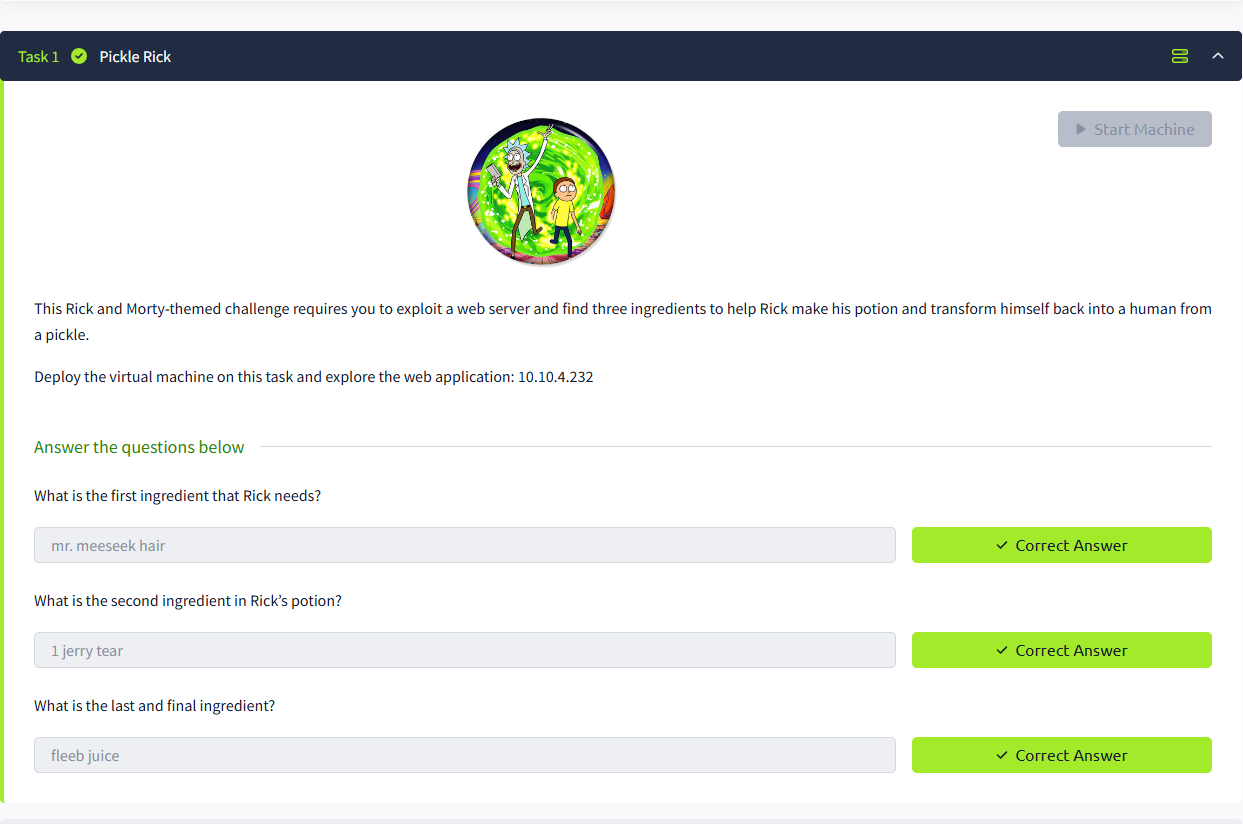
With all of the flags now collected and submitted, the room was complete. It was an interesting room, not overly stressing but a good reminder of basics - e.g. permissions, linux commands and how to scan a system for information and vulnerabilities.
As an added bonus, I even made it into the Top 10 names for the room. I'm not quite sure how the metrics are calculated, but I'll take it as a win.
Tune in next time for another hacking adventure!