Generating Every UK Mobile Phone Number.
A reflection on experimental code I wrote to generate every UK mobile phone number.
At the outset, I should make clear the code being discussed here could be used in highly unethical ways, and I do not endorse or recommend using it in malicious or unethical capacities nor do I accept any responsibility for those who do so. The same could be said for tools like FlipperZero or O.MG Cable, but although they have malicious uses, they have legitimate uses too. On my part, I am publishing this for my own recollection and education, but also because I find the application of code in this way interesting.
Hypothesis
Last year, I was staying with family who were getting nuisance calls on a fairly regular basis. After a while, I started to wonder how the callers were getting the numbers they dialled. It seemed to me that buying the numbers could be one route, but that would be pretty expensive and doubtful the best way. They could collect data or scavenge for it in data dumps/leaks, but this is equally time consuming, not to mention potentially unethical/illegal... but then again, these people probably weren't worried about ethics or legalities.
Taking the lack of ethics or legalities into consideration, it would also be possible that the numbers were simply being generated programmatically. I thought about this for a little while and wondered how hard it would be to generate every UK mobile phone number. After supping up the coffee I was drinking, I figured it wouldn't actually be that hard.
We have a format to follow, for example, each mobile number begins with two digits - 07 - followed by three sets of three digits - 000 + 000 + 000. In that sense, it's basic mathematics, we begin at 000000000 because it is the lowest value, and end at 999999999, because that is the highest value available.
To generate the numbers, we create a loop to iterate and add the prefacing two digits to the relevant generated number. For example - 07 + 000 000 000.
Implementation
To implement the code, I opened Visual Studio and created a .NET Console Application. This was just an experiment so I just needed a console to show the output from the program for which a console application fit perfectly.
Once the console application solution was open, I considered the hypothesis.
Obviously, we have fixed starting numbers (07) which can be added to the start of any generated numbers simply by creating them adding them to a Console.WriteLine with double quotes.
Then there are the multiple sets of ending numbers. The simplest way to generate every mobile number would be to simply count up from 000000000 or down from 999999999, but that could take a long time on a single thread and adding multi-threaded code for a quick experiment was probably a bit OTT, so I felt a quicker "hacky" way to get around this way to simply break down the numbers into batches.
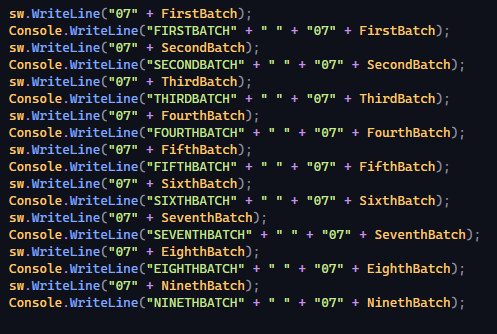
Enter the batches -
int FirstBatch = 999999999;
int SecondBatch = 899999999;
int ThirdBatch = 799999999;
int FourthBatch = 699999999;
int FifthBatch = 599999999;
int SixthBatch = 499999999;
int SeventhBatch = 399999999;
int EighthBatch = 299999999;
int NinethBatch = 199999999;
Each batch was thrown into a main loop which counted down if i was a lower value than FirstBatch which, it always would be because I had set i to equal 0. In adding all of the batches to the loop, 9 numbers were generated per loop. One of the downsides to this was that eventually, there would be duplicates generated.
The numbers were outputted to the console, but to test the hypothesis, I also saved numbers to an output file. These were deleted after the test.
Results
I left the code running for about 14 hours. In that time, it generated a text file that was about 8gb in size containing millions of numbers. That's not quite the hundreds of millions, or nearly billion that would be needed to generate all UK mobile phone numbers but it represents proof that it is possible with not very much code.
To verify that these were real numbers, I took a hand full at random and added them as contacts. Most popped up on Whatsapp. There were a variety of people, often times displaying personal information and alarmingly, children, in their photos or bios. Perhaps this is a reminder that anyone can be watching and looking at any time.
All of the numbers were subsequently deleted.
Conclusion
This was a fun experiment and confirmed my hypothesis that numbers are most likely being generated by scammers instead of bought. I say that because it's incredibly easy and quite cheap to do, and would certainly be more advantageous than attempting to get data from data leaks - although I suppose there is value to be had from genuine data leaked in dark parts of the web.
In terms of the code itself, if I were to write the application again, I would move to a multi-threaded approach and handle the output better. It was also pointed out to me via a helpful commenter on facebook after I posted this blog that 000 is not a valid prefix for mobile numbers, so some more validation might be in order which would cut down any bogus numbers generated.
This time around, I found the generation somewhat slow which is probably because the loop was executing single threaded on my CPU rather than taking full advantage of my GPUs. I'm not using particularly sluggish hardware, but it would be good to optimise. Similarly, the numbers were dumped into one long list which, although it suited the purpose of the experiment, is not very human friendly or useful.
After thoughts
Outside of the scope of the experiment, I think generating phone numbers in this capacity raises a lot of questions about privacy and security. If I, as a then 30 year old, can generate millions of UK Mobile numbers in a bedroom on my desktop, we have to ask what can Police, Mi5, Mi6, GCHQ and the Military do - or more likely, have done? but also, what can foreign adversaries and the criminal underground do?
I raise the "powers that be" first and foremost because over the years, we have seen legislation put forward in the UK (and in other allied nations, especially 5 eyes affiliated) that significantly broadens the scope of espionage and surveillance powers, but also policing and terror powers. These are mostly put forward under the guise of protecting children, women or stopping sexual predators, but can be manipulated when suited. It therefore stands to reason that they will already have a full list of every UK mobile and landline number and be passively monitoring including bulk SMS collection under Tempora.
Of course, this experiment can be carried across into every other nation in the sense it's possible to generate every American, German, Dutch, Swiss, Russian, Australian (ad infinitum) number, just as it is UK numbers.
The problem arising from that is that any celebrity, politican, journalist, judge, CEO or basically, any person connected to any number on the planet is reachable - if you can find the right number in the haystack.
Finding the number is a bit more of a challenge, but certainly not an impossibility. For example, GCHQ ran a programme under the codename BABYLON which ran bulk queries against webmail addresses (mainly Hotmail and Yahoo). If the address was registered, BABYLON would highlight that it was in use by providing a green tick next to the address. It then follows, that if GCHQ were trying to find a certain person, they would sift through the data collected by BABYLON for addresses that might be related to the person or objective. If you're interested in the types of programmes being run by GCHQ, check out this Full list of codenames and programmes
It's important to highlight that BABYLON was run indiscriminately - so it targeted innocent persons as well as those whom might be a national security risk. Linking back to passive monitoring,
The process would be the same for finding a person attached to a number because there's a reasonable presumption that they would be signed up for, lets say, Whatsapp, Signal, Telegram, Facebook, Twitter and so on.
Taking the generated numbers as a starting point and connecting the dots with other platforms and available information should be fairly trivial. Of course, this does pose a risk because we have already seen communication via whatsapp from Downing street and I have personally witnessed Police officers, Social Workers, Family Workers and Executives communicating via Whatsapp.
There should be a presumption that these agents of the state are being monitored by foreign adversaries for personal vulnerabilities, but also any weaknesses in cyber security to give those adversaries an "in" to Public Sector systems - e.g. the Legal Aid System hack recently, which saw every single person who had claimed legal aid since 2010 have their data leaked.
On the one hand, we face increasingly draconian law regarding online safety but the practicalities of tech and in a sense, the mathematics, make the laws almost redundant especially when dealing with foreign adversaries and those outside our borders, or indeed, those work in a grey area in terms of the law and ethics. On the other, we must ensure everyone is taking Cyber Security seriously and that Government and the public sector are secure, proactively thinking about "smaller" threats like these.
That's where I'm going to leave you, dear reader. Hopefully a little bit frightened and uneasy, but questioning if you're not technical, and especially if you work in the public sector or you run a business of your own. If you felt yourself getting a bit tetchy that someone might have your number who you didn't want to have it, just keep in mind that this is very, very basic mathematics and there are much worse, more invasive systems in existence. We need a serious talk in the United Kingdom about Cyber Security, Privacy and the risks, but I'll save that for another blog.